Challenge description
This .tar file got tarred a lot.
Category: Forensics
Solution
As the challenge noted, the file for this challenge is a tar archive, I confirmed that fact just in case using the file command.
Looking at the file using a file manager, it appears that this archive is deeply nested.
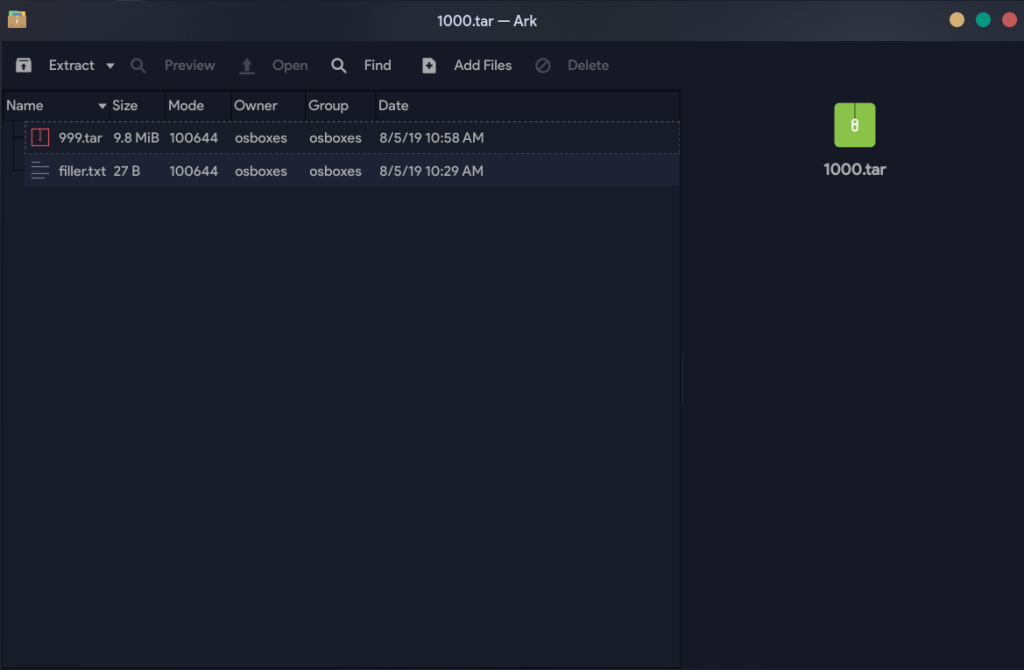
The task at hand is most likely to extract these nested archives until we reach the end (presumably after 999 extractions). So off I went on a search for a tool to do so. The built-in tar command doesn’t seem up to the task, although perhaps that is just because of my inexperience. My search on the Internet did not fair much better, as the closest thing I found was an old python2 script from 2011.
While pondering my next steps, I remembered that binwalk, a tool I regularly use for these types of forensic challenges, includes a module to extract files. Let’s try that.

binwalk -eUsing the -e option to extract the file, the result is identical to manually extracting the files. Not very helpful. Looking through the application’s help pages, however, I discovered an option to recursively look through the extraction results and extract whatever is there. This seems perfect for the job.
In the end, I settled with binwalk -Mer. With these options, I will be able to extract the archives recursively, while also removing the original file to avoid clutters.
But it’s not smooth sailing just yet. After a minute or so of letting binwalk run, it encountered an error and stopped.
OSError: [Errno 36] File name too long:
Looks like because binwalk was reading the path recursively, the path got a little too long for it to handle after a few hundred iterations.
My (completely inelegant) solution to this was just to navigate to wherever binwalk stopped at using my file manager (only a few seconds of holding down the Enter key), retrieving the archive, and running the command again.
Roughly 4 or 5 attempts later, I finally got to the flag, it was, as expected, hidden at the deepest level.

From then, we simply have to view the flag.png file to obtain the flag 🏁
Notes
There are definitely better ways to solve this challenge without having to manually navigate to the destination folder each time binwalk errors out.
Two options crossed my mind, either update the old python2 script I found at the beginning, or modify the underlying python module that binwalk was using to extract files. As of now, I am nowhere near proficient enough with python to attempt either of those options, but in the future, who knows, perhaps it would make a nice personal project.
